Table of Contents
The Quantum Computing Revolution
A brief overview of quantum computing and how it's different from classical computing
Let's talk about quantum computing.
First introduced in the 1980s by famed physicist Richard Feynman, quantum computing uses the principles of quantum mechanics to process information.
Instead of using classical bits (0s and 1s), quantum computers use "quantum bits," called qubits. Due to the phenomenon known as superposition, qubits can represent both 0 and 1 simultaneously.
Here is a simple analogy without going too deep:
Superposition is like a quarter spinning on a table. While spinning, it is neither heads nor tails but a combination of both possibilities until it finally lands on one side. With quantum computing, the quarter can effectively be both heads and tails at the same time.
This concept allows quantum computers to perform multiple calculations in parallel, potentially solving problems exponentially faster than classical computers.
If you want to get a primer on physics and the concepts of quantum mechanics, check out Richard Feynman's book called Six Easy Pieces (while the concepts are still very advanced, Richard makes them easier to understand than any other resource I've ever read).
The Benefits of Quantum Computing
The benefits of quantum computing can include the following:
A seismic escalation of technology advancements across the board
Advancements in cryptography and Artificial Intelligence machine-learning capabilities
Improved search algorithms for large data sets - searching over a set of possible outcomes for complex pattern prediction and simulations
Factoring large numbers and performing complex scientific calculations
This revolutionary computing shift could lead to an exponential threat landscape shift for the world.
Economic Impact of Quantum Computing
The potential economic impact of quantum computing is staggering. Projections suggest it could unlock billions or even trillions in value across various sectors. Enhancements and optimizations in material and life sciences, chemicals, pharmaceutical research, the automotive industry, and more could help humankind make gigantic leaps forward.
A study by McKinsey & Company from April 2023 highlighted that quantum computing could generate an annual value of $620 billion to $1.3 trillion.
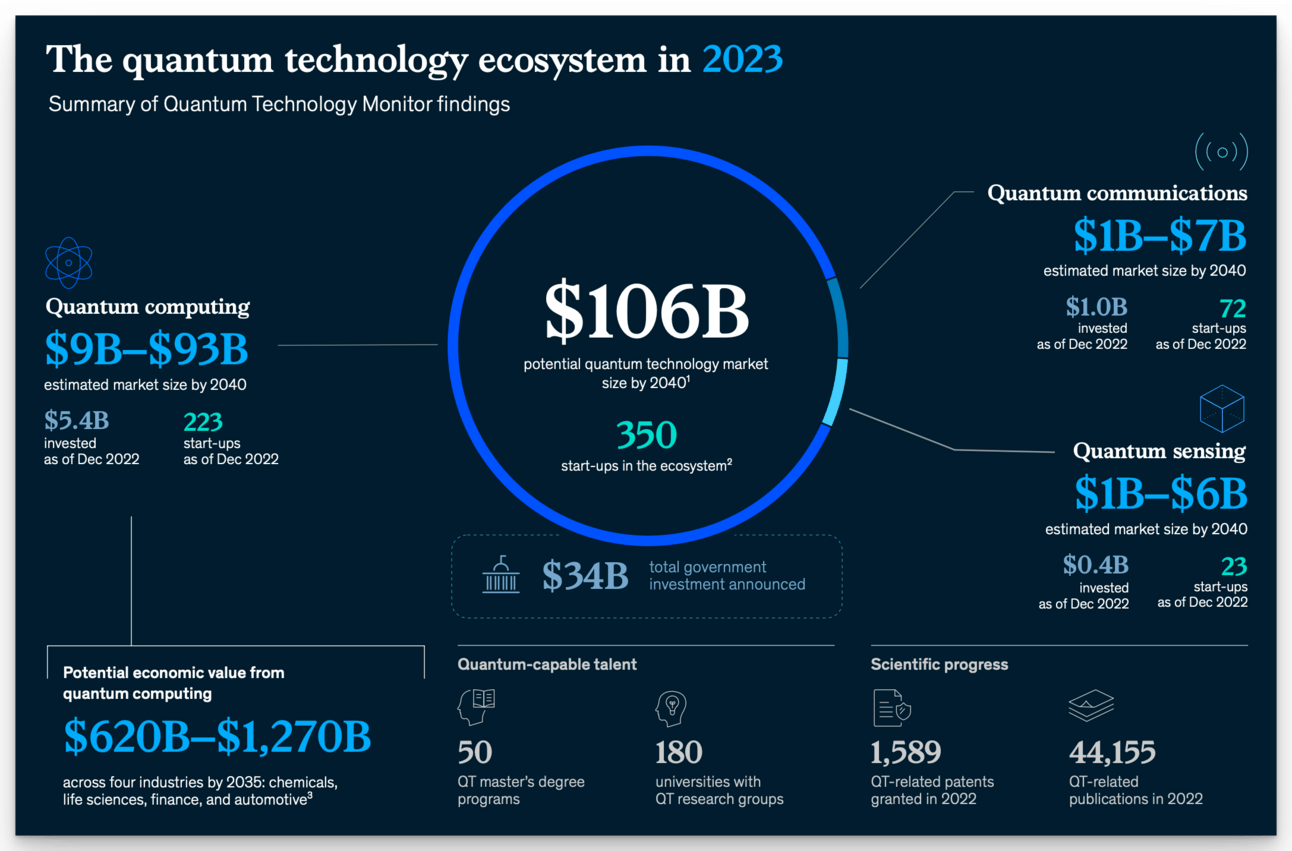
The potential for these advancements alone underscores the critical need for quantum security measures to protect economic interests and maintain competitive advantages.
Potential Concerns about Advancements in Quantum Computing
With quantum computing will come unknown levels of computational power. It's not hard to imagine the misuse of that level of power by bad actors, and some concerns are:
Breaking current technology and security protections across the world
Potential national security concerns with military and economic imbalances
Advances of Nation State attack capabilities
Limiting other country's abilities to access new technologies and developmentally stunting nations
Increased mass surveillance and spying
This revolutionary computing shift could lead to an exponential threat landscape shift for the world.
Quantum Security: Building a Multi-Layered Defense
The Rising Importance of Quantum Security
Quantum security is an emerging field of cybersecurity that is just starting to be understood. Once quantum computing is more broadly available, quantum security will focus on providing protection and encryption for data and communications.
The current applications of quantum security are all about making other things “quantum-resistant.”
|
Term: Quantum-Resistant Pronunciation: KWON-tuhm ree-ZIS-tuhnt Definition: Technologies built to safeguard digital data against the computational capabilities of emerging quantum computers. |
Some of those methods include:
Post-Quantum Cryptography (PQC) - implementing new cryptographic algorithms based on new mathematical problems, structures, and implementations to be quantum-resistant.
Quantum Key Distribution (QKD) - using quantum computing to generate new encryption keys that cannot be replicated or broken due to the nature of quantum entanglement, making it quantum resistant.
Quantum Random Number Generation (QRNG) - a method for generating truly random numbers using the unpredictable nature and laws of quantum mechanics instead of deterministic methods used by traditional computing, making it quantum-resistant.
What is Potentially at Risk with Quantum Computing?
Quantum computers have the potential to break several encryption standards due to their ability to solve complex mathematical problems much faster than classical computers. This includes:
Email, chat, and SMS messaging
Browser encryption
Mobile app connections
Encrypted passwords and hashes
Any SSL/TLS encryption and public key cryptography using RSA and Elliptic Curve Cryptography (ECC)
Simply put, encryption algorithms are based on math, and quantum computers will be the world's best mathematicians.
So what can we do about it?
Prepping Your Business for Quantum Computing
Practical Steps Toward Quantum Readiness
While still largely theoretical in many aspects, once it does become "real," it may be too late. Defense-in-depth still remains true. There is a strong change your executive team is already hearing scary stories about the "disastrous effects that quantum computing will bring, so it's a good idea to start having these conversations in your companies.
How should you think about applying defense-in-depth practices to quantum security? Here are a few things you can do to get yourself prepared as a cybersecurity organization:
Educate stakeholders - Raise awareness among decision-makers about the importance of quantum security and the need for investment in quantum-resistant solutions.
Focus on a data protection strategy - discover and manage all keys, leverage various methods of de-valuing data (tokenization), and have an accurate inventory of your data.
Evaluate your scope - inventory the cryptographic risks across your organization and 3rd parties (i.e., find out where there are weaker key lengths or algorithms used).
Scale up your standards - update internal encryption standards, increase key sizes for symmetric and asymmetric keys, and remove weak ciphers from your scope.
Data retention - ensure policies and procedures are in place to destroy confidential data once records are no longer required.
Collaborate with experts: Engage with industry leaders and researchers in quantum computing and security to facilitate the development and implementation of cutting-edge solutions.
Quantum Threats Mapped to STRIDE
Threat model out what the risks might be. If you're not familiar with Threat Modeling, it can be best described as:
A structured representation of all the information that affects the security of an application. In essence, it is a view of the application and its environment through the lens of security
STRIDE is a popular threat modeling framework, and here is a non-exhaustive list of quantum computing threats mapped to this framework.
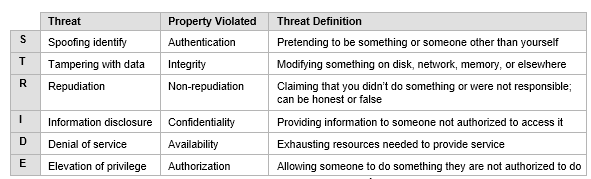
STRIDE evaluates the system detailed design and models the in-place system. It builds data-flow diagrams (DFDs) to identify system entities, events, and boundaries.
Here are a few examples using STRIDE to threat model for quantum computing applications:
This is just a place where you can start to think through the ramifications and come up with an approach. It’s better to have some planning instead of not planning for these kinds of things.
Key Players and Innovators in Quantum Security
Who is Working on Quantum Security?
Various organizations and initiatives are developing quantum-resistant encryption methods and securing digital assets against quantum threats:
National Institute of Standards and Technology (NIST): is working on the Post-Quantum Cryptography Standardization project to identify and standardize quantum-resistant cryptographic algorithms.
European Telecommunications Standards Institute (ETSI): a Quantum Safe Cryptography (QSC) working group dedicated to researching and developing quantum-resistant cryptographic standards.
PQCRYPTO Project: an EU-funded initiative to develop and analyze post-quantum cryptographic algorithms.
Open Quantum Safe (OQS): an open-source project that aims to provide quantum-safe cryptographic solutions, including libraries and tools for developers to implement and test quantum-resistant encryption.
Microsoft Quantum Development Kit (QDK): resources for learning and experimenting with quantum-resistant cryptographic algorithms and tools for developing quantum applications.
IBM Quantum Experience: a cloud-based quantum computing platform with resources for learning about quantum cryptography and experimenting with quantum algorithms.
Google Quantum AI: resources and tools for learning about quantum computing and quantum cryptography, as well as experimenting with quantum algorithms.
Staying informed about these developments and engaging with the resources provided by these organizations will help in preparing for the quantum era.
Other References
Wrapping Up
I hope you've enjoyed this perspective on quantum security challenges and learned something new. Because this is an extremely technical concept, I did not go very deep into the terminology, which is very academic at this point. The references I mentioned above will let you dig deeper into any of these topics.
This post isn't intended to be an exhaustive list of threats and best practices but a general point of view and orientation to help prep yourself and your company. This space will change so fast, so please let me know if I missed something.

