Security, Funded by is a weekly intelligence briefing of the public and private economic activity in the cybersecurity market. This week’s issue is brought to you by Axonius.
As if the acquisition spree of identity companies from two weeks ago didn’t convince you that AI Agent identity is everything right now, there were even more acquisitions to that tune last week.
AI model companies are rapidly launching AI Agentification of Work across messaging platforms, AI-driven browsers, and even in the places where real work happens (Excel). And as exciting as that is, the public cyber heavyweights are launching their own assault on capability acquisition.
But it’s not just the big dogs making moves. AI acquisition moves are being made across the maturity spectrum, as there is still much to sort out in the arena.

PARTNER
You Can’t Act on What You Don’t Trust
90% of security teams say they’re ready to respond—yet only 25% trust their asset data. Don't let incomplete visibility break your response.
Axonius delivers trusted asset intelligence to prioritize exposures and act with confidence.

Table of Contents

😎 Vibe Check
Click the options below to vote on whether you are a practitioner, founder, or investor. Feel free to leave a comment, and I'll feature the best takes in next week’s write-up!
What security problem is criminally underfunded?
Last issue’s vibe check:
Is AI finally solving the problem of tool integration in cyber?
🟨🟨⬜️⬜️⬜️⬜️ Yes, AI is bridging what other platforms couldn't
🟨🟨🟨🟨⬜️⬜️ It helps, but the mess underneath remains
🟩🟩🟩🟩🟩🟩 No, it's just another layer that doesn't integrate
🟨🟨🟨⬜️⬜️⬜️ Too early, ask me in 2027
Well, there you have it, folks. Sadly, it seems AI has not yet solved all of security’s tool-integration challenges. I do see this getting better over time, and it’s going to require some rethinking and retooling to make these future states a reality.
<rant> My personal opinion on solving challenges with AI is that the entire industry has been thinking far too macro for most problems for too long. The more you use AI to build things, the more you realize that you have to go lower and lower, and make the problem space smaller and smaller. More guardrails, more rules, more precedents, and more discrete blocks of work are needed to be successful.
The tools that win in the future won’t be the ones that solve these large, esoteric problems (at least not for a very long time), but it’ll be the ones that solve the small headaches that make operating or achieving things an order of magnitude easier in a coordinated way. But you’ve got to start smaller than you initially think. </rant>
Some of the top comments from last week’s vibe check:
💬 “A security stack is like an ogre. Like an ogre, it has layers. Then the analogy stops because each layer irritates the other layers it’s sandwiched by.”
Never thought I’d see a security-Shrek-themed comment in the vibe check, but damn if I’m not here for it. 🧅 👹

💰 Market Summary
Private Markets
12 companies from 5 countries raised $435.1M across 8 unique product categories
Average deal size was $43.5M (median: $30.0M)
100% of funding went to product companies
12 companies from 6 countries were acquired for $420.0M across 9 unique product categories
58% of M&A activity went to product companies
Public Markets
No public cyber companies had an earnings report in the first few weeks of 2026
U.S. stocks were down inside and outside of cyber due to the announcement of a criminal investigation into the U.S. Federal Reserve Chair, further challenging the Fed’s independence in controlling monetary policy.

As of markets close on January 16, 2026.

📸 YoY Snapshot
Rolling 13-week charts that compare funding and acquisitions week over week, year over year, comparing 2024 vs. 2025 and 2025 vs. 2026.

Funding is picking right back up where it left off in 2025 with a really strong week, and several companies coming out of stealth.
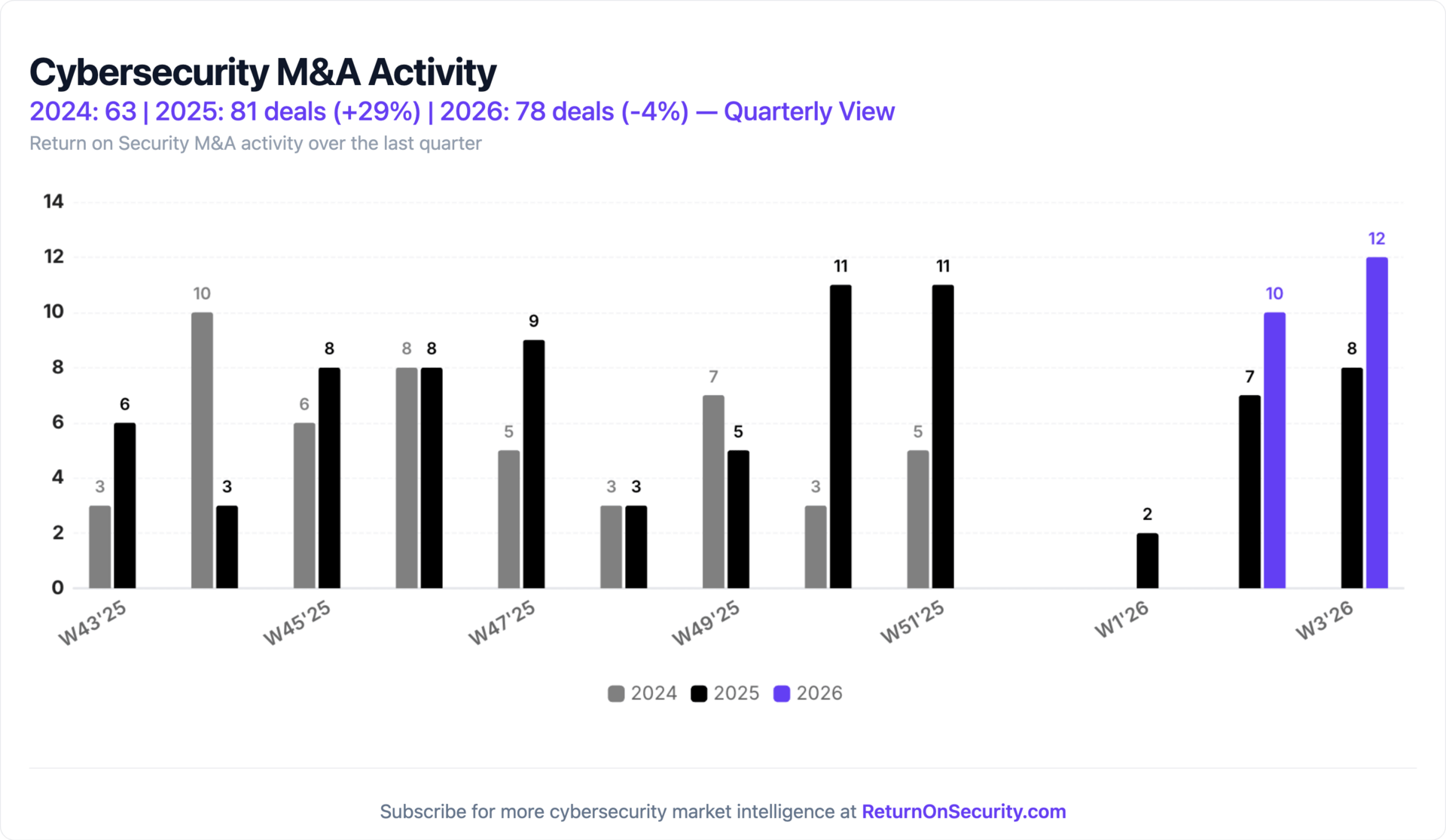
M&A is just continuing to ripe, even for a time of year when transactions are usually higher than normal.


☎️ Earnings Reports
This analysis is personal research and opinions only. This is not financial or investing advice. Do your own due diligence before making investment decisions.
Earnings reports from last week: None
Earning reports to watch this coming week: None

🧩 Funding By Product Category
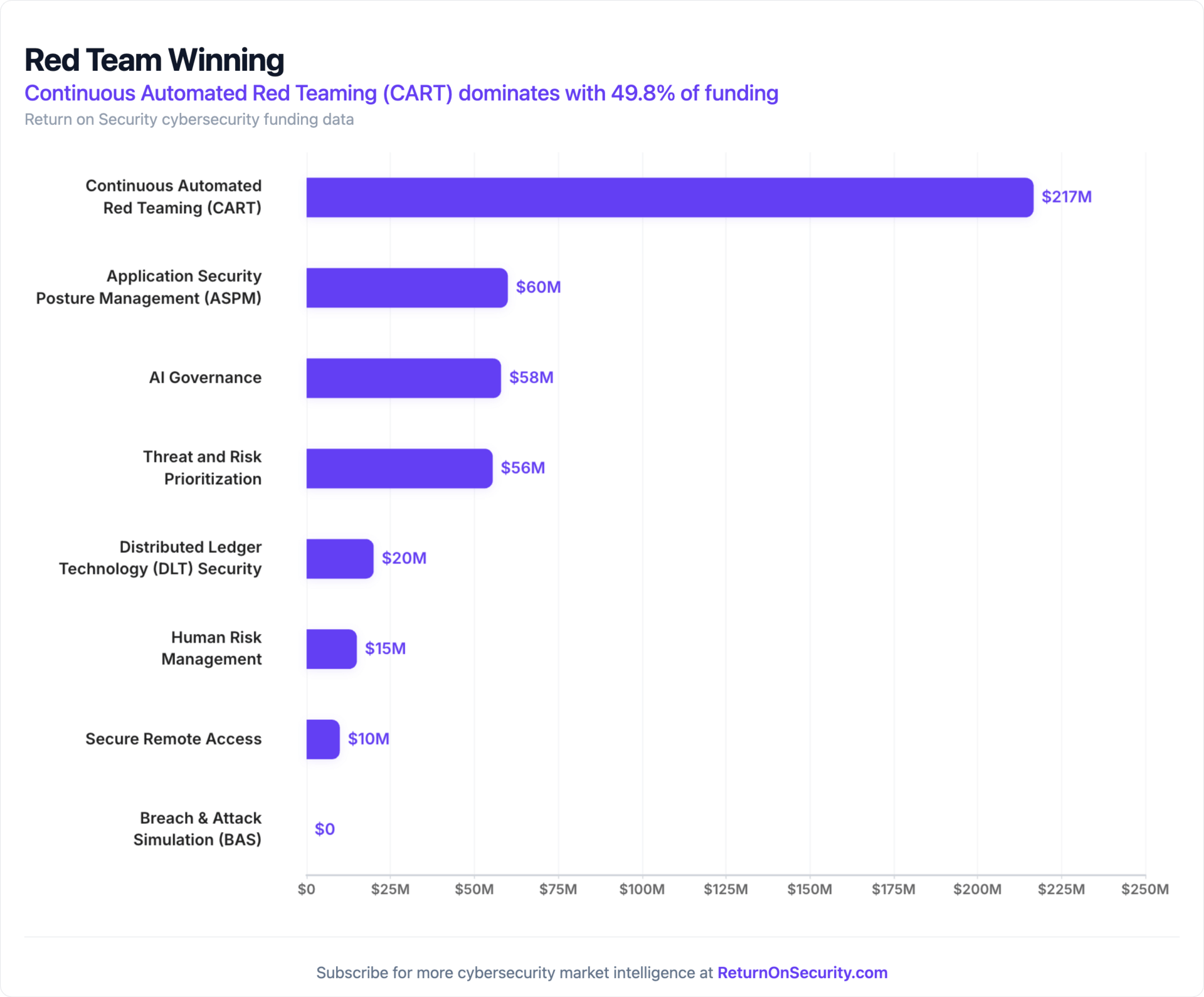
$216.7M for Continuous Automated Red Teaming (CART) across 2 deals
$60.0M for Application Security Posture Management (ASPM) across 1 deal
$58.0M for AI Governance across 1 deal
$55.5M for Threat and Risk Prioritization across 4 deals
$20.0M for Distributed Ledger Technology (DLT) Security across 2 deals
$15.0M for Human Risk Management across 1 deal
$9.9M for Secure Remote Access across 1 deal
An undisclosed amount for Breach & Attack Simulation (BAS) across 1 deal

🏢 Funding By Company
Product Companies:
Armadin Security, a United States-based automated red-teaming and AI threat hunting platform, raised a $165.2M Venture Round. (more)
Aikido Security, a Belgium-based application security posture management (ASPM) platform, raised a $60.0M Series B from DST Global. (more)
WitnessAI, a United States-based AI governance and safety platform, raised a $58.0M Venture Round from Sound Ventures. (more)
Novee Security, an Israel-based continuous automated red teaming and penetration testing platform, raised a $51.5M Seed from YL Ventures, Canaan Partners, and Oren Zeev. (more)
depthfirst, a United States-based threat and risk prioritization platform, raised a $40.0M Series A from Accel. (more)
Project Eleven, a United States-based platform for migrating blockchain networks to post-quantum cryptographic standards, raised a $20.0M Series A from Castle Island Ventures. (more)
Zepo, a Spain-based human risk management and security awareness platform, raised a $15.0M Seed from Kibo Ventures, eCAPITAL ENTREPRENEURIAL PARTNERS, and TIN Capital. (more)
CloudSEK, a Singapore-based externally focused threat and risk prioritization platform , raised $10.0M Series B from Connecticut Innovations and an undisclosed Secondary Market transaction. (more)
NetBird, a United States-based open-source secure remote access platform, raised a $9.9M Series A from Pace Capital. (more)
Fencer, a United States-based threat and risk prioritization platform for software and SaaS companies, raised a $5.5M Seed from MHS Capital. (more)
Horizon3.ai, a United States-based breach and attack simulation platform, raised an undisclosed Venture Round from Prosperity7 Ventures. (more)
Naoris Protocol, a United States-based Web3 application security platform, raised an undisclosed Corporate Round from MOVA Chain. (more)
Service Companies:
None

🌎 Funding By Country

$298.6M for the United States across 8 deals
$60.0M for Belgium across 1 deal
$51.5M for Israel across 1 deal
$15.0M for Spain across 1 deal
$10.0M for Singapore across 2 deals

🤝 Mergers & Acquisitions

Product Companies:
Seraphic Security, an Israel-based remote enterprise browser isolation platform, was acquired by CrowdStrike for $420.0M. Seraphic Security had previously raised $29.0M in funding. (more)
DeceptIQ, a United Kingdom-based deception technology platform based on red-team hunting and attacker analysis, was acquired by Thinkst Canary for an undisclosed amount. DeceptIQ has not previously disclosed any funding events. (more)
MCP Manager, a United States-based gateway for deploying, monitoring, and managing MCP servers and external AI applications, was acquired by Usercentrics for an undisclosed amount. MCP Manager has not previously disclosed any funding events. (more)
Service Companies:
Beyond Secure, a United States-based managed security services and professional services provider, was acquired by nuview for an undisclosed amount. Beyond Secure has not previously disclosed any funding events. (more)
Brite, a United States-based managed XDR security services provider, was acquired by Sole Source Capital for an undisclosed amount. Brite has not previously disclosed any funding events. (more)
NetSource One, a United States-based managed security services provider, was acquired by New Charter Technologies for an undisclosed amount. NetSource One has not previously disclosed any funding events. (more)

📚 Great Reads
The Death of the Ticket - How AI is Redefining Security Engineering for SMBs and tech companies.
Trail of Bits Skills Marketplace - Trail of Bits published some very cool Claude Code skills for security research, vulnerability detection, and audit workflows.
*A message from our partners

🧪 Labs

Security ROI > Coffee ROI
Get value every week? Back the mission.
Or send your smart friends a referral.

Data Methodology and Sources
All of the data is captured point-in-time from publicly available sources.
All financial figures are converted to U.S. Dollars (USD) at the current spot rate at the time of collection.
Company country locations are pulled from publicly available sources.
Companies are categorized using the Return on Security system.
Sometimes the deal details, such as who led the round, how much was raised, or the deal stage, may be updated after publication.
Let us know if you spot any errors, and we’ll fix them.



