Security, Funded is a weekly deep dive into cybersecurity funding and industry news captured and analyzed by Mike Privette. This week’s issue is presented together with Outpost24 and Material Security.
Hey there,
I’m riding on a high-speed train from London to Scotland as I write the newsletter opener this week, which got me thinking about how riding trains has taught me a lot about B2B Sales is a super cool sentence for me to say.
It’s a good time for a long weekend trip, too. The VC industry has hit its annual “cool-down” period, kicking off with Burning Man and ending with Labor Day in the US. This means there are fewer transactions than normal for a few weeks as the industry changes gears into the back half of the year. Combine this cooling off period with inflation in the US hitting a new 3-year low last week, all but sealing an interest rate cut next month, and it’s just about time to get some of that dry powder wet. 🏂
🚨 Speaking of dry powder, with only a handful of spots left in 2024, I am officially opening up sponsorship slots for the 2025 season!
Join me in reaching 10,000+ of the brightest cybersecurity leaders and decision-makers from around the world.
Just email [email protected] to see how we can partner together! 💪
Onward to this week's issue.

TOGETHER WITH
New AI Domain Discovery Tool within External Attack Surface Management
Know your attack surface and effortlessly identify domains belonging to your organization
With the new AI Domain Discovery feature in Outpost24’s External Attack Surface Management solution, you can now effortlessly identify domains belonging to your organization and significantly improve the speed and accuracy of domain ownership and classification.
Get a free attack surface analysis and discover the simplicity of mapping your expanding attack surface. With EASM, you can analyze all your known and unknown internet-facing assets for vulnerabilities and attack paths.

Table of Contents

😎 Vibe Check
As we are now well into the second half of the year, what is your security program's top priority for the rest of the year?
Last issue’s vibe check:
Are you still vibing the Vibe Check section?
🟩🟩🟩🟩🟩🟩 ✅ Hell yeah bröther (58)
⬜️⬜️⬜️⬜️⬜️⬜️ ❌ It's a no from me dawg (5)
63 Votes
Hell yeah, bröthers and sïsters! Thanks to everyone who voted last week and all the weeks that you took the time to vote in these vibe checks. Let’s keep this train rolling!
Some of the top comments from last week:
“love seeing the comments/thoughts from others as well!”
“I love the vibe check! Keep it comin', bröther”
“Return on Security is running wild, brother!”

💰 Market Summary
5 companies raised $459.1M across 4 unique product categories in 2 countries
4 companies were acquired or had a merger event across 4 unique product categories
80% of funding went to product-based cybersecurity companies
No public cyber companies had an earnings report

📸 YoY Snapshot
This is a rolling 12-week chart comparing funding and acquisitions each week in a year-over-year (YoY) view between 2023 and 2024.
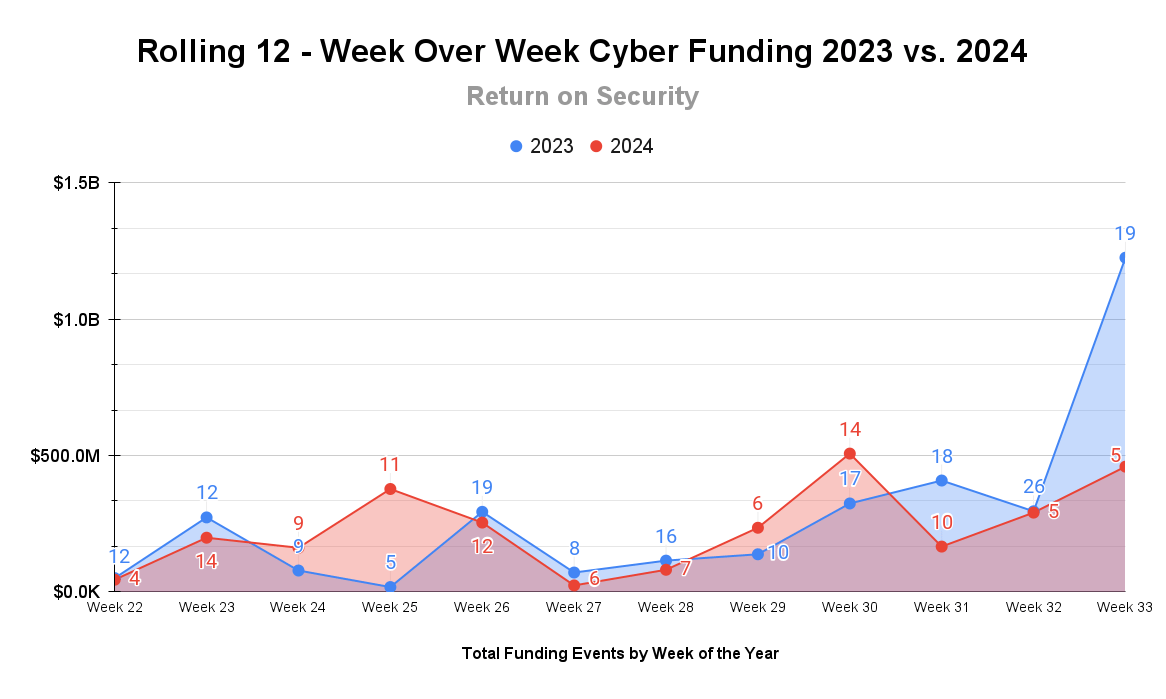
Fewer rounds this week continue but with greater impact. While this time last year looked really different, the numbers were disproportionately skewed by a $1 billion post-IPO debt round. Taking that large round out, this week's numbers are about double what we saw last year. Incidentally, we can say the same thing about this week in funding next year.
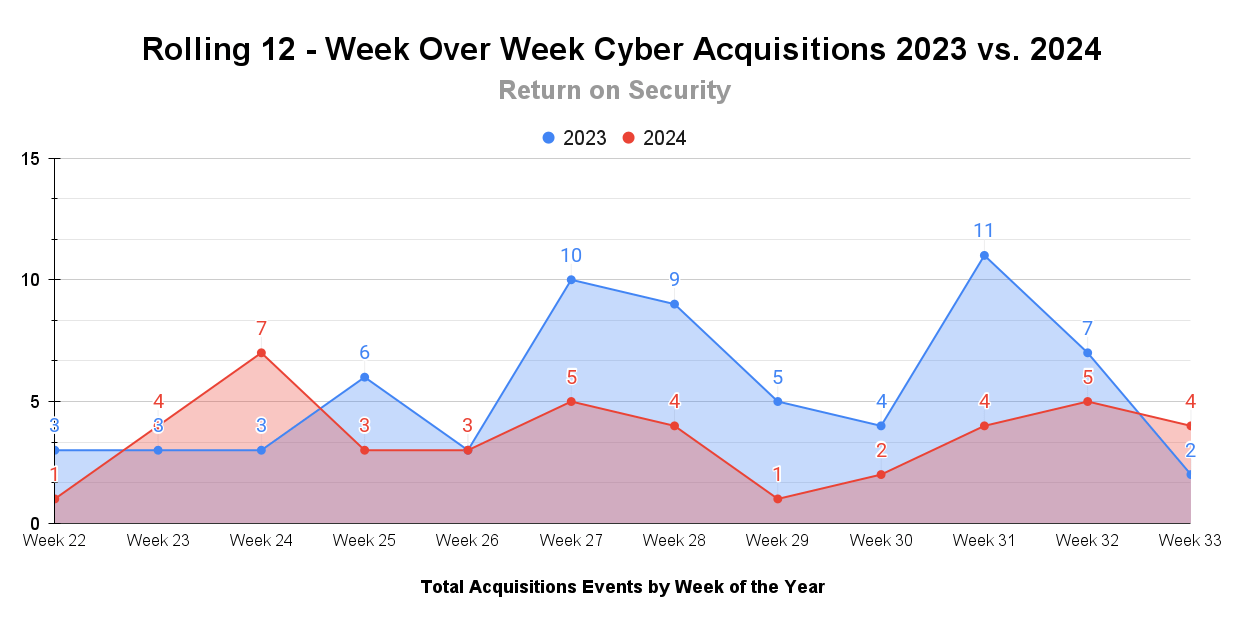
M&A has continued on a slower and steadier pace this year, and last week was no exception.

🤙 Earnings Reports
Here are notable earnings reports from public cybersecurity companies. This section is Powered by Quartr, where I track all the latest earning reports.
Earnings reports this week: None
As always, the public cyber company tracker shows all public cybersecurity companies worldwide, along with market data, funding raised, product categories, and more!


🧩 Funding By Product Category
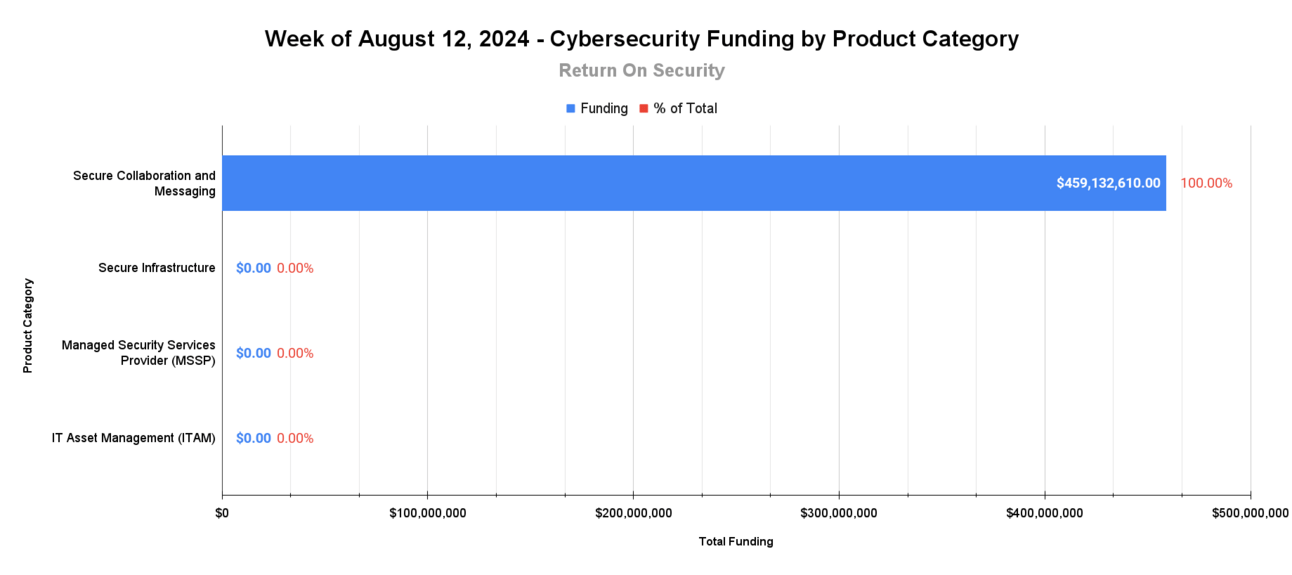
$459.1M for Secure Collaboration and Messaging across 2 deals
An undisclosed amount for Secure Infrastructure across 1 deal
An undisclosed amount for Managed Security Services Provider (MSSP) across 1 deal
An undisclosed amount for IT Asset Management (ITAM) across 1 deal

🏢 Funding By Company
Kiteworks, a United States-based secure data collaboration and messaging solutions suite, raised a $456.0M Private Equity Round from Insight Partners and Sixth Street. (more)
Alpaca Networks, a South Korea-based secure hosting and infrastructure platform, raised an undisclosed Grant from the TIPS Program.
Ideal Integrations, a United States-based managed security services provider (MSSP), raised an undisclosed Private Equity Round from Frontenac Company. (more)
Sepio, a United States-based physical-layer IT asset discovery and inventory platform, raised an undisclosed Series B from Tau Capital. (more)

🌎 Funding By Country
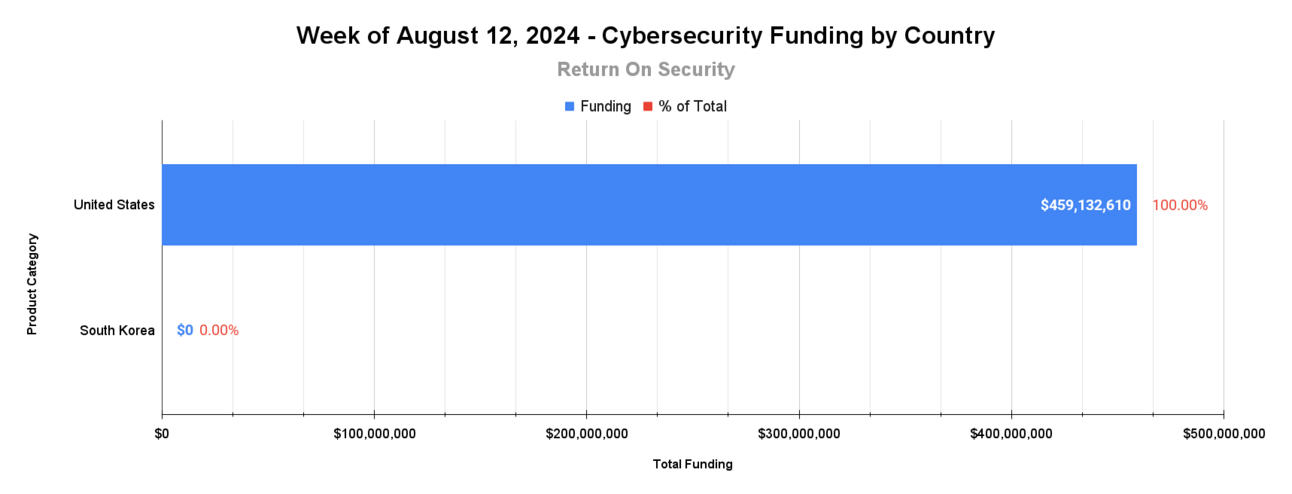
$459.1M for the United States across 4 deals
An undisclosed amount for South Korea across 1 deal

🤝 Mergers & Acquisitions

Cyber Trust Alliance, a United States-based professional services firm focused on cyber risk assessments, was acquired by CorePLUS Technologies for an undisclosed amount. (more)
Safe Systems, a United States-based managed security services provider (MSSP), was acquired by UFS for an undisclosed amount. (more)

📚 Great Reads
Reflections on Black Hat 2024 - My friend Francis Odum shares his key takeaways from more than 100 conversations with founders, investors, and operators.
*How to help your security team drowning in phishing alerts - A write-up on how to save your security team hours each week while making your email security more effective.
In the Beginning was the Command Line - A short essay by my favorite author, Neal Stephenson, on operating systems, the cultural implications of technology, and how it has evolved over the years.
State of Exploitation - A Peek into 1H-2024 Vulnerability Exploitation - I'm a sucker for data crunching and good visuals, and this vulnerability exploitation report for the first half of 2024 does not disappoint.
*A message from our sponsor

🧪 Labs
Organized crime via sprints and retrospectives adds more shareholder value.

How was this week's newsletter?

Data Methodology and Sources
All of the data is captured point-in-time from publicly available sources.
All financial figures are converted to U.S. dollars (USD) when collected.
Company country locations are pulled from publicly available sources.
Companies are categorized using our system at Return on Security, and we write all the company descriptions.
Sometimes, the details about deals, like who led the round, how much money was raised, or the deal stage, might get updated after the issue is first published.
Let us know if you spot any errors, and we’ll fix them.

About Return on Security
Return on Security is all about breaking down the cybersecurity industry for you with expert analysis, hard facts, and real-life stories. The goal? To keep security pros, entrepreneurs, and investors ahead in a fast-moving field. Read more about the “Why” here.
Feel free to borrow any data, charts, or advice you find here. Just make sure to give a shoutout to Return on Security when you do.

Thank you for reading. If you liked this analysis, please share it with your friends, colleagues, and anyone interested in the cybersecurity market.

