Security, Funded provides a weekly analysis of economic activity in the cybersecurity market. This week’s issue is presented together with Harmonic Security and Nudge Security.
Hey there,
Hope you had a great weekend and are getting back into the swing of the new year!
This week’s issue will be slightly different, just like last week’s issue. Consider this first issue covering the start of 2025 from January 1st until January 12th. After this week, I’ll move back to the business-as-usual cadence of covering just the previous week’s activity.
Also, I made a small update to the referral program, which now only requires one referral to get access to the full database of Great Reads links since the very first issue. Check it out here ({{ rp_refer_url }} ), and please be sure to share with someone who you think will find this newsletter valuable!

TOGETHER WITH
Is 2025 The Year to Move Past Blocking GenAI?
This is the year your AI committee moves from blockers to builders. Your competitors aren’t waiting to use GenAI—and neither should you.
Adopt GenAI in a smart way with Harmonic Security:
Give employees the right guardrails to securely adopt GenAI
Identify Shadow AI and GenAI tools training on your data
Detect sensitive data leaving the business via GenAI apps
Coach users via inline training and nudging towards safe AI use
Nudge your AI committee to embrace GenAI’s potential with the right safeguards in place.

Table of Contents

😎 Vibe Check
How is your organization’s cybersecurity function perceived at the executive level?
Last issue’s vibe check:
What’s the biggest driver for your company’s investment in “AI for Security” or “Security for AI”?
🟨⬜️⬜️⬜️⬜️⬜️ Addressing talent shortages (8)
🟩🟩🟩🟩🟩🟩 Automating manual security processes (24)
🟨⬜️⬜️⬜️⬜️⬜️ Enhancing threat detection and response (6)
🟨⬜️⬜️⬜️⬜️⬜️ Staying competitive in the market vs. peers (6)
44 Votes
Far and away last week, people said that their main AI and Security use case was around automating manual security processes. This should come as no surprise, as the sheer amount of effort and context required to make security decisions has only increased (which will likely always be true). Baked into this, in my opinion, is the inherent driver of “doing more with the same.”
Intelligent augmentation and automation are what everyone wants and needs out of the AI & Security space (the basics), so start here, and then we can get to some more advanced use cases later if, and only if (!), we can solve the basics.
Some of the top comments from last week:
Threat detection - “We want our automation to be deliberate, thought out, but the work of quick statistical analysis of device behavior is beyond most of our current capabilities -- ML helps here greatly”
Automation - “Most of the manual things we are using AI for is documentation and security packages. The stuff that requires you to type things out but is fairly static and reproducible. I would actually call it automation more than AI, but here we are.”

💰 Market Summary
6 companies raised $64.3M across 5 unique product categories in 5 countries
9 companies were acquired or had a merger event across 7 unique product categories
100% of funding went to product-based cybersecurity companies
No public cyber companies had an earnings report

📸 YoY Snapshot
This is a rolling 12-week chart comparing funding and acquisitions each week in a year-over-year (YoY) view between 2024 and 2025.

A slower first few weeks of the year as we ease into 2025. Given that 2024 landed up higher than 2023 on the funding front overall, I’m not surprised we have a quieter start these first two weeks.

M&A, on the other hand, is already ripe and ready to go. In 2024, there were more M&A transactions than in 2023, and I’m calling it early that 2025 will follow the same playbook.


☎️ Earnings Reports
Cyber Market Movers

As of markets close on January 10, 2025
Earnings reports from last week: None
Macro Context:
A bit of a mixed bag overall coming into the new year.
Tech markets (which account for most of the S&P500 gains) were down slightly in the last days of 2024, partly due to the SEC's still inconsistent treatment of cryptocurrencies and regulation.
US employers added 256,000 jobs in December 2024, cruising past expectations per the Labor Department’s monthly report. The US Federal Reserve is now likely to hold interest rates steady or even increase rates again due to a faster-than-expected jobs market.
There are also broad concerns about increased inflation due to the upcoming tariffs that US President Donald Trump will put in place.
Earning reports to watch this coming week:
None

🧩 Funding By Product Category
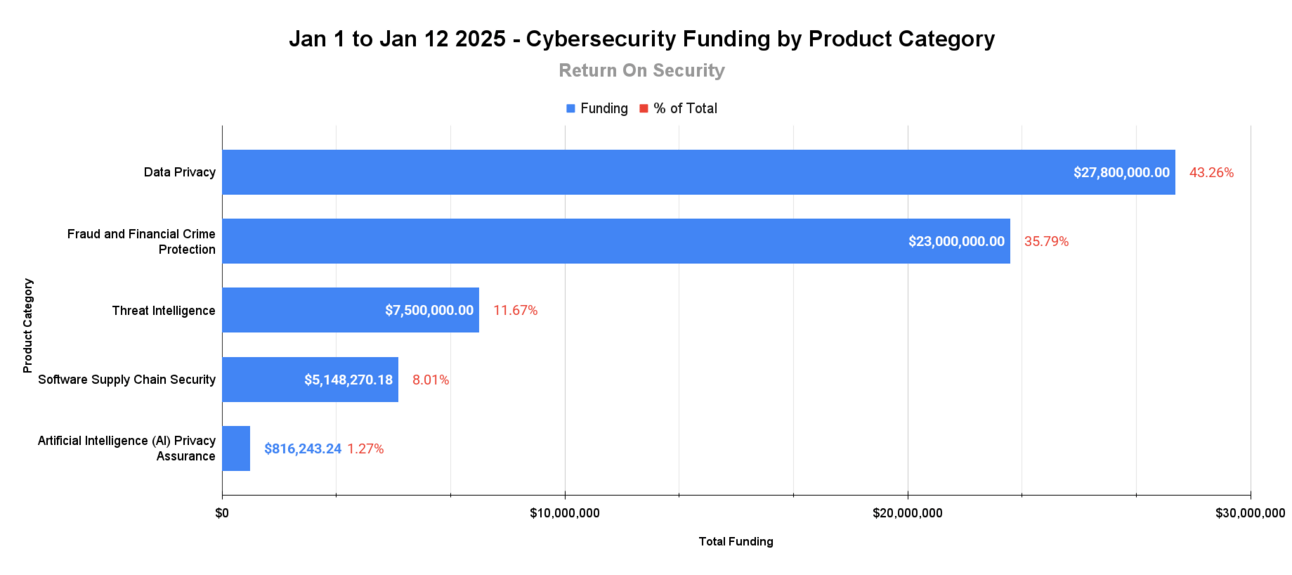
$27.8M for Data Privacy across 2 deals
$23.0M for Fraud and Financial Crime Protection across 2 deals
$7.5M for Threat Intelligence across 1 deal
$5.1M for Software Supply Chain Security across 1 deal
$816.2K for Artificial Intelligence (AI) Privacy Assurance across 1 deal

🏢 Funding By Company
Apheris, a Germany-based data privacy and governance platform, raised a $20.8M Series A from eCaptial and OTB Ventures. (more)
ThreatMark, a Czech Republic-based fraud and financial crime protection platform, raised a $15.0M Venture Round from Octopus Ventures and Riverside Acceleration Capital and an $8.0M Convertible Note from Springtide Ventures. (more)
Intrusion, a United States-based cyber threat intelligence platform, raised a $7.5M post-IPO equity round.
Dataships, an Ireland-based data privacy software and services company, specializing in automating GDPR and CCPA compliance, raised a $7.0M Series A from Osage Venture Partners. (more)
SignPath, an Austria-based software supply chain security platform, raised a $5.1M Series A from TIIN Capital. (more)
CyberTide, a Germany-based AI privacy assurance platform for chatbot applications and foundational LLMs, raised a $816.0K Grant from the German Federal Ministry of Education and Research.

🌎 Funding By Country

$23.0M for Czech Republic across 2 deals
$21.6M for Germany across 2 deals
$7.5M for United States across 1 deal
$7.0M for Ireland across 1 deal
$5.1M for Austria across 1 deal

🤝 Mergers & Acquisitions

360 Advanced, a United States-based professional services firm focused on cyber risk management services, was acquired by Bregal Sagemount for an undisclosed amount. 360 Advanced has not publicly disclosed any prior funding rounds. (more)
Cado Security, a United Kingdom-based cloud digital forensics platform, was acquired by Darktrace for an undisclosed amount. Cado Security had previously raised $31.5M in funding. (more)
Kivu, a United States-based professional services firm focused on cyber incident response services, was acquired by Quorum Cyber for an undisclosed amount. Kivu had not publicly disclosed any prior funding rounds. (more)
Nclose, a South Africa-based managed security services provider (MSSP), was acquired by Integrity360 for an undisclosed amount. Nclose has not publicly disclosed any prior funding rounds. (more)
Qryptonic, a United States-based professional services firm focused on quantum-resistant encryption assessments, was acquired by SpringOwl Technology Partners for an undisclosed amount. Qryptonic has not publicly disclosed any prior funding rounds. (more)
Zero-Shot Security, a United States-based security operations support platform focused on automated MITRE ATT&CK mappings, was acquired by Tidal Cyber for an undisclosed amount. Zero-Shot Security has not publicly disclosed any prior funding rounds. (more)

📚 Great Reads
The Weirdest Tech Products for CES 2025 - The weirdest, silliest, and most eyebrow-raising products from CES 2025. Some of these are nightmare fuel!
*How GLAAD protects SaaS identities and sensitive data with Nudge Security - With Nudge, the team at GLAAD got immediate visibility into SaaS they hadn’t known about and saved 4-5 hours per day in manual effort while improving their SaaS security posture.
Compliance and its Uses - Compliance serves as a strategic tool but isn’t a guarantee of security, as evidenced by PCI-compliant firms suffering breaches. This post prioritizes tailored security strategies over strict compliance adherence to optimize risk mitigation and business outcomes.
Leadership in Cybersecurity: A Guide to Your First Role - My friend Lawrence Munro wrote a piece about how the demand for leadership training in cybersecurity remains unmet. Over 70% of new leaders struggle due to inadequate mentorship and unclear expectations.
*A message from our sponsor

🧪 Labs
How was this week's newsletter?

Data Methodology and Sources
All of the data is captured point-in-time from publicly available sources.
All financial figures are converted to U.S. dollars (USD) when collected.
Company country locations are pulled from publicly available sources.
Companies are categorized using our system at Return on Security, and we write all the company descriptions.
Sometimes, the details about deals, like who led the round, how much money was raised, or the deal stage, might get updated after the issue is first published.
Let us know if you spot any errors, and we’ll fix them.

About Return on Security
Return on Security is all about breaking down the cybersecurity industry for you with expert analysis, hard facts, and real-life stories. The goal? To keep security pros, entrepreneurs, and investors ahead in a fast-moving field. Read more about the “Why” here.
Feel free to borrow any data, charts, or advice you find here. Just make sure to give a shoutout to Return on Security when you do.

Thank you for reading. If you liked this analysis, please share it with your friends, colleagues, and anyone interested in the cybersecurity market.


